Wep Cracker Windows
Internet has become one of the most important requirement of today’s life. In fact, for some of us, it is the source of income. With the increasing use of Internet and handy devices like smartphone and tablet and other smart gadgets that make use of internet almost all the things are made available online in digital form.
Gone are the days when people used to stay connected with others using their Internet data pack, To access Internet you need your laptop, desktop or smartphone.
This is the reason people prefer to have wireless connection in homes and offices in order to connect all the devices and work efficiently. Even in your neighbor, school, college or office premises, you must have encountered Wi-Fi networks but it is true that you can’t use them unless you have the correct WiFi password of it. Most of the networks are secured with password key so that no person other than authorized ones could use or access it for free.
Must visit: How To Find Out WiFi Password Of Your WiFi Network
Crack WEP encrypted networks. Crack WPA encrypted networks. Support for multiple interfaces. Network scan. Packet Injection. Fake authentication. (Open and Shared key) Mac address changer. Discovery of hidden SSIDs; WEP Dictionary attack; Password generator for WPA networks; Frontend for Qt and Gtk. Wep0ff is new WEP Key Cracker that can function without access to AP, it works by mounting a fake access point attack against WEP-based wireless clients. It uses a combination of fragmentation and evil twin attacks to generate traffic which can be used for KoreK-style WEP-key recovery. Fern WiFi Wireless Cracker is another nice tool which helps with network security. It lets you see real-time network traffic and identify hosts. Basically this tool was developed to find flaws in computer networks and fixes the detected flaws. It is available for Apple, Windows and Linux platforms.
Wep crack free download - Crack Killer, WEP and WPA keygenerator, Ubiquiti airMAX WEP Connector, and many more programs. Crack The Lock for Windows 10.
I know how it feels when you are close to any Internet connection and can’t access it because of that password. Even if your own network is down, you desperately want to connect to neighboring Wi-Fi network in order to carry out the tasks.
But can you do anything to get past this? Can you access any Wi-Fi network without password? Well, yes if it is done through good Wi-Fi password cracker software. So, we are going to know about the best software for your Windows PC or laptop to crack Wi-Fi password. Let’s have a look.
Top 5 Wi-Fi Password Cracker Software for Windows
1. Aircrack
Apr 08, 2013 WEPCrack is a tool that cracks 802.11 WEP encryption keys using the latest discovered weakness of RC4 key scheduling. AirSnort is a wireless LAN tool which cracks encryption keys on 802.11b WEP networks. This software works well with Linux and Microsoft Windows for decrypting WEP encryption on 802.11b network. AirSnort saves data in two formats. First, all the packets captured by AirSnort is saved in pcap dump file. Oct 19, 2010 aircrack-ng – for recovering the WEP key; Start Aircrack-ng GUI and select the log file from above. Also select the encryption(WEP) and Key size (64). Press launch and the WEP key will be revealed.
Aircrack is one of the most popular wireless password cracking tools that provides 802.11a/b/g WEP and WPA cracking. The software uses best algorithms to recover the password of any wireless network by capturing packets, once the enough packets from any wireless network gathered; the software tries to recover the password.
Aircrack works well with Windows, Linux, OS X, Open BSD, NetBSD, Solaris and more.
2. Smartkey WiFi Password Recovery
This is actually a Wifi password recovery app but you can use WiFi Password recovery as a hacking software to hack WiFi password of a WiFi connection. It is a very powerful WiFi password hacking tool for Windows. The software claims to crack any type of high security WiFi password.
The software provides 5 different attack methods to crack password of a WiFi. The attaks are: dictionary attack, word attack, mask attack, combination attack and hybrid attack to crack the WiFi password.
The dictionary attack tries every word from the dictionary to crack the password. Word attack tries all the anagrams and mutations of a word. Mask attack is used when you have some knowledge of the WiFi password. For example, the length of password, starting letter, ending letter, number of vowels, etc.
Combination attack uses all possible mutations of two words and the hybrid attack tries all the mutations of the dictionary. You can even provide more than one dictionary to crack the WiFi password.
3. Kismet
Kismet is a network detector, packet sniffer and intrusion detection software for 802.11 wireless LANs that supports raw monitoring mode and sniff 802.11a, 802.11b, 802.11g and 802.11n traffic.
Kismet sniffs and captures packets of wireless network in order to determine username and password. You can also use Kismet to identify hidden network and sniff into other connected systems as Kismet features the ability to detect default or non-configured networks and determine what level of wireless decryption needs to be done on a given access point.
Kismet comes with three separate parts, drone to collect the packets of any wireless network, server in connection with drone to interpret packet data and extrapolating wireless information and the client that communicates with server and displays all the information collected by server.
4. AirSnort
AirSnort is a wireless LAN tool which cracks encryption keys on 802.11b WEP networks. This software works well with Linux and Microsoft Windows for decrypting WEP encryption on 802.11b network. AirSnort saves data in two formats. First, all the packets captured by AirSnort is saved in pcap dump file. It also saves data to capture session in the form of crack files.
Running AirSnort is quiet easy, once launched AirSnort must be configured to work with wireless NIC so that it could make attempts to crack password. AirSnort operates by passively monitoring the entire transmissions and computing the encryption key as soon as enough packers are gathered.
5. NetStumbler
NetStumbler basically known as Network Stumbler is Windows tool that detects 802.11b, 802.11a, 802.11g wireless LANs. NetStumbler is used to verify wireless network configuration, detecting cause of wireless interface, detecting unauthorized access points, wardriving, finding location with poor network security and more.
NetStumbler comes with a little disadvantage that it can be easily detected by most of the wireless intrusion detection system.
Do you know about any better WiFi password cracker software? Let me know through comments.
Cracking WEP, WPA-PSK and WPA2-PSK wireless security using aircrack-ng
2008-11-21 (updated: 2013-02-25) by Philip
Tags: aircrack, Wireless, Wi-Fi, WPA, WEP, WPA2, NIC, hash, wordlist, security, SSID, channel, crack, hack, reaver, WPS, vulnerability
Introduction
With the popularity of wireless networks and mobile computing, an overall understanding of common security issues has become not only relevant, but very necessary for both home/SOHO users and IT professionals alike. This article is aimed at illustrating current security flaws in WEP/WPA/WPA2.
Successfully cracking a wireless network assumes some basic familiarity with networking principles and terminology, as well as working with command-line tools. A basic familiarity with Linux can be helpful as well.
Disclaimer: Attempting to access a network other than your own, or one you have permission to use is illegal insome U.S. jurisdictions. Speed Guide, Inc. are not to be held liable for any damages resulting from the use or misuse of the information in this article.
To successfully crack WEP/WPA, you first need to be able to set your wireless network card in 'monitor' mode to passively capture packets without being associated with a network. This NIC mode is driver-dependent, and only a relatively small number of network cards support this mode under Windows.
One of the best free utilities for monitoring wireless traffic and cracking WEP/WPA-PSK keys is the aircrack-ng suite, which we will use throughout this article. It has both Linux and Windows versions (provided your network card is supported under Windows). The aircrack-ng site has a comprehensive list of supported network cards available here: NIC chipset compatability list.
If your network card is not supported under Windows, one can use a free Linux Live CD to boot the system. BackTrack is probably the most commonly used distribution, since it runs from a Live CD, and has aircrack-ng and a number of related security auduting tools already installed.
For this article, I am using aircrack-ng on another Linux distro (Fedora Core) on a Sony Vaio SZ-680 laptop, using the built-in Intel 4965agn network card. If you're using the BackTrack CD aircrack-ng is already installed, with my version of linux it was as simple as finding it with:
yum search aircrack-ng
yum install aircrack-ng
The aircrack-ng suite is a collection of command-line programs aimed at WEP and WPA-PSK key cracking. The ones we will be using are:
airmon-ng - script used for switching the wireless network card to monitor mode
airodump-ng - for WLAN monitoring and capturing network packets
aireplay-ng - used to generate additional traffic on the wireless network
aircrack-ng - used to recover the WEP key, or launch a dictionary attack on WPA-PSK using the captured data.
1. Setup (airmon-ng)
As mentioned above, to capture network traffic wihtout being associated with an access point, we need to set the wireless network card in monitor mode. To do that under linux, in a terminal window (logged in as root), type:
iwconfig (to find all wireless network interfaces and their status)
airmon-ng start wlan0 (to set in monitor mode, you may have to substitute wlan0 for your own interface name)
Note: You can use the su command to switch to a root account.
Other related Linux commands:
ifconfig (to list available network interfaces, my network card is listed as wlan0)
ifconfig wlan0 down (to stop the specified network card)
ifconfig wlan0 hw ether 00:11:22:33:44:55 (change the MAC address of a NIC - can even simulate the MAC of an associated client. NIC should be stopped before chaning MAC address)
iwconfig wlan0 mode monitor (to set the network card in monitor mode)
ifconfig wlan0 up (to start the network card)
iwconfig - similar to ifconfig, but dedicated to the wireless interfaces.
2. Recon Stage (airodump-ng)
This step assumes you've already set your wireless network interface in monitor mode. It can be checked by executing the iwconfig command. Next step is finding available wireless networks, and choosing your target:
airodump-ng mon0 - monitors all channels, listing available access points and associated clients within range. It is best to select a target network with strong signal (PWR column), more traffic (Beacons/Data columns) and associated clients (listed below all access points). Once you've selected a target, note its Channel and BSSID (MAC address). Also note any STATION associated with the same BSSID (client MAC addresses).
running airodump-ng displays all wireless access points and associated clients in range, as well as MAC addresses, SSIDs, signal levels and other information about them. |
WEP is much easier to crack than WPA-PSK, as it only requires data capturing (between 20k and 40k packets), while WPA-PSK needs a dictionary attack on a captured handshake between the access point and an associated client which may or may not work.
3. Capture Data (airodump-ng)
To capture data into a file, we use the airodump-ng tool again, with some additional switches to target a specific AP and channel. Most importantly, you should restrict monitoring to a single channel to speed up data collection, otherwise the wireless card has to alternate between all channels. Assuming our wireless card is mon0, and we want to capture packets on channel 6 into a text file called data:
airodump-ng -c 6 bssid 00:0F:CC:7D:5A:74 -w data mon0 (-c6 switch would capture data on channel 6, bssid 00:0F:CC:7D:5A:74 is the MAC address of our target access point, -w data specifies that we want to save captured packets into a file called 'data' in the current directory, mon0 is our wireless network adapter)
Running airodump-ng on a single channel targeting a specific access point |
Notes:
You typically need between 20,000 and 40,000 data packets to successfully recover a WEP key.
One can also use the '--ivs' switch with the airodump-ng command to capture only IVs, instead of whole packets, reducing the required disk space. However, this switch can only be used if targeting a WEP network, and renders some types of attacks useless.
4. Increase Traffic (aireplay-ng) - optional step for WEP cracking
An active network can usually be penetrated within a few minutes. However, slow networks can take hours, even days to collect enough data for recovering the WEP key.
This optional step allows a compatible network interface to inject/generate packets to increase traffic on the wireless network, therefore greatly reducing the time required for capturing data. The aireplay-ng command should be executed in a separate terminal window, concurrent to airodump-ng. It requires a compatible network card and driver that allows for injection mode.
Assuming your network card is capable of injecting packets, in a separate terminal window try:
aireplay-ng -3 -b 00:0F:CC:7D:5A:74 -h 00:14:A5:2F:A7:DE -x 50 wlan0
-3 --> this specifies the type of attack, in our case ARP-request replay
-b ... --> MAC address of access point
-h ... --> MAC address of associated client from airodump
-x 50 --> limit to sending 50 packets per second
wlan0 --> our wireless network interface
aireplay-ng allows for injecting packets to greatly reduce the time required to recover a WEP key |
Notes:
To test whether your nic is able to inject packets, you may want to try: aireplay-ng -9 wlan0. You may also want to read the information available -here-.
To see all available replay attacks, type just: aireplay-ng
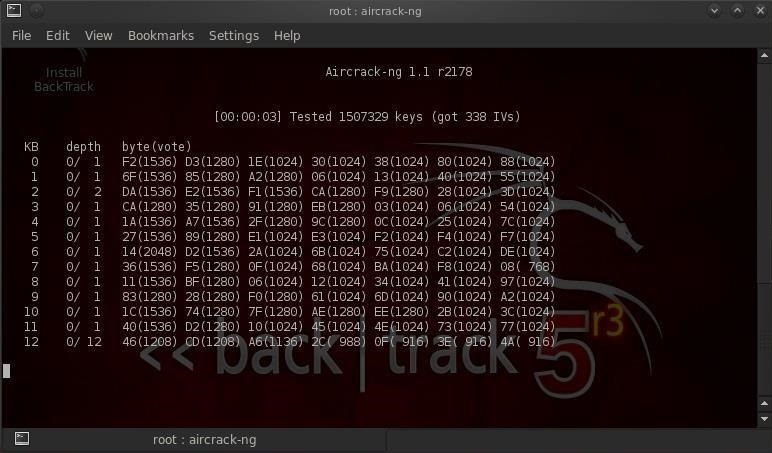
5. Crack WEP (aircrack-ng)
WEP cracking is a simple process, only requiring collection of enough data to then extract the key and connect to the network. You can crack the WEP key while capturing data. In fact, aircrack-ng will re-attempt cracking the key after every 5000 packets.
To attempt recovering the WEP key, in a new terminal window, type:
aircrack-ng data*.cap (assuming your capture file is called data..cap, and is located in the same directory)
aircrack-ng can successfully recover a WEP key with 10-40k captured packets. The retreived key is in hexadecimal, and can be entered directly into a wireless client omitting the ':' separators |
Notes:
If your data file contains ivs/packets from different access points, you may be presented with a list to choose which one to recover.
Usually, between 20k and 40k packets are needed to successfully crack a WEP key. It may sometimes work with as few as 10,000 packets with short keys.
6. Crack WPA or WPA2 PSK (aircrack-ng)
WPA, unlike WEP rotates the network key on a per-packet basis, rendering the WEP method of penetration useless. Cracking a WPA-PSK/WPA2-PSK key requires a dictionary attack on a handshake between an access point and a client. What this means is, you need to wait until a wireless client associates with the network (or deassociate an already connected client so they automatically reconnect). All that needs to be captured is the initial 'four-way-handshake' association between the access point and a client. Essentially, the weakness of WPA-PSK comes down to the passphrase. A short/weak passphrase makes it vulnerable to dictionary attacks.
To successfully crack a WPA-PSK network, you first need a capture file containing handshake data. This can be obtained using the same technique as with WEP in step 3 above, using airodump-ng.
You may also try to deauthenticate an associated client to speed up this process of capturing a handshake, using:
aireplay-ng --deauth 3 -a MAC_AP -c MAC_Client mon0 (where MAC_IP is the MAC address of the access point, MAC_Client is the MAC address of an associated client, mon0 is your wireless NIC).
The command output looks something like:
12:34:56 Waiting for beakon frame (BSSID: 00:11:22:33:44:55:66) on channel 6
12:34:56 Sending 64 directed DeAuth. STMAC: [00:11:22:33:44:55:66] [ 5:62 ACKs]
Note the last two numbers in brackets [ 5:62 ACKs] show the number of acknowledgements received from the client NIC (first number) and the AP (second number). It is important to have some number greater than zero in both. If the first number is zero, that indicates that you're too far from the associated client to be able to send deauth packets to it, you may want to try adding a reflector to your antenna (even a simple manilla folder with aluminum foil stapled to it works as a reflector to increase range and concentrate the signal significantly), or use a larger antenna.
Simple antenna reflector using aluminum foil stapled to a manilla folder can concentrate the signal and increase range significantly. For best results, you'll have to place the antenna exactly in the middle and change direction as necessary. Of course there are better reflectors out there, a parabolic reflector would offer even higher gain, for example. |
Once you have captured a four-way handshake, you also need a large/relevant dictinary file (commonly known as wordlists) with common passphrases. See related links below for some wordlist links.
You can, then execute the following command in a linux terminal window (assuming both the dictionary file and captured data file are in the same directory):
aircrack-ng -w wordlist capture_file (where wordlist is your dictionary file, and capture_file is a .cap file with a valid WPA handshake)
Additional Notes:
Cracking WPA-PSK and WPA2-PSK only needs 4 packets of data from the network (a handshake). After that, an offline dictionary attack on that handshake takes much longer, and will only succeed with weak passphrases and good dictionary files. A good size wordlist should be 20+ Megabytes in size, cracking a strong passphrase will take hours and is CPU intensive.
Cracking WPA/WPA2 usually takes many hours, testing tens of millions of possible keys for the chance to stumble on a combination of common numerals or dictionary words. Still, a weak/short/common/human-readable passphrase can be broken within a few minutes using an offline dictionary attack. My record time was less than a minute on an all-caps 10-character passphrase using common words with less than 11,000 tested keys! A modern laptop can process over 10 Million possible keys in less than 3 hours.
WPA hashes the network key using the wireless access point's SSID as salt. This prevents the statistical key-grabbing techniques that broke WEP, and makes hash precomputation more dificult because the specific SSID needs to be added as salt for the hash. There are some tools like coWPAtty that can use precomputed hash files to speed up dictionary attacks. Those hash files can be very effective (sicne they're much less CPU intensive and therefore faster), but quite big in size. The Church of WiFi has computed hash tables for the 1000 most common SSIDs against a million common passphrases that are 7Gb and 33Gb in size..
7. Crack WPA using the WPS Vulnerability (Reaver)
Many Wi-Fi devices are aslo vulnerable to a WPS (Wi-Fi Protected Setup) vulnerability described in US-CERT TA12-006A Alert. WPS provides simplified mechanisms to secure wireless networks, most often using a PIN as a shared secret to authenticate clients and share the WEP/WPA/WPA2 passwords and keys. The external PIN exchange mechanism is susceptible to brute-force attacks that allow for bypassing wireless security in a relatively short time (few hours). The only remedy is to turn off WPS, or use an updated firmware that specifically addresses this issue.
A free Linux open-source tool called Reaver is able to exploit the WPS vulnerability. To launch an attack:
1. Install Reaver - http://code.google.com/p/reaver-wps/
2. Set your network adapter in monitor mode as described above, using:
ifconfig wlan0 down
iwconfig wlan0 mode monitor
ifconfig wlan0 up
Alternatively, you can put your network card in monitor mode using: airmon-ng start wlan0 (this will produce an alternate adapter name for the virtual monitor mode adapter, usually mon0 )
3. Before using Reaver to initiate a brute-force WPS attack, you may want to check which access points in the area have WPS enabled and are vulnerable to the attack. You can identify them using the 'wash' Reaver command as follows:
wash -i mon0 --ignore-fcs
4. Run Reaver (it only requires two inputs: the interface to use, and the MAC address of the target)
reaver -i mon0 -b 00:01:02:03:04:05 -vv
Wep Crack Windows 10
There are a number of other parameters that one can explore to further tweak the attack that are usually not required, such as changing the delay between PIN attempts, setting the tool to pause when the access point stops responding, responding to the access point to clear out failed attempts, etc. The above example adds '-vv' to turn on full verbose mode, you can use '-v' instead for fewer messages. Reaver has a number of other switches (check with --help), for example ' -c11' will manually set it to use only channel 11, ' --no-nacks' may help with some APs.
5. Ez-pass license plate type. Spoof client MAC address if needed. In some cases you may want/need to spoof your MAC address. Reaver supports MAC spoofing with the --mac option, however, for it to work you will have to change the MAC address of your card's physical interface (wlan0) first, before you specify the reaver option to the virtual monitor interface (usually mon0). To spoof the MAC address:
ifconfig wlan0 down
ifconfig wlan0 hw ether 00:11:22:33:44:55
ifconfig wlan0 up
airmon-ng start wlan0
reaver -i mon0 -b .. -vv --mac=00:11:22:33:44:55
An attack using Reaver typically takes between 4 and 8 hours (provided WPS requests are not being limited by the AP), and returns the SSID, WPS PIN and WPA passphrase for the target network. Note that some routers may lock you out for a few minutes if they detect excessive failed WPS PIN attempts, in such cases it may take over 24 hours.
Notes:
Some routers (including most popular Cisco/Linksys models) will NOT turn off WPS even if turned off via the radio button in their web admin interface. You may be able to turn it off using third-party firmware, such as DD-WRT (wich does not support WPS).
Reportedly, some models/vendors/ISPs all come configured with a default pin. Common pins are 12345670, 00005678, 01230000, etc. Reaver attempts known default pins first.
Reaver comilation requires libpcap (pcap-devel) and sq3-devel (sqlite3-dev) installed, or you will get a 'pcap library not found' error.
Troubleshooting Tips
Even with the above tools properly installed, it is common to get a few errors/warnings during the attacks, usually related to timeouts, poor signal, or interface driver not supporting monitor/injection modes. Here are some points to consider:
1. Is your adapter properly set in monitor mode ?
2. Does the adapter driver support injection (is aireplay-ng working) ?
3. Do you have to spoof your MAC address (if AP limits MACs, change both physical and virtual monitor interface) ?
4. Do you have a good signal to the AP ?
5. Do you see associated clients (for WPA handshake capture) ?
6. Do you see WPS pin count incrementing (Reaver WPA cracking) ?
7. Does the target AP support WPS and is it enabled (for WPS attacks, check with the 'wash' command) ?
Final Thoughts
As demonstrated above, WEP cracking has become increasingly easier over the years, and what used to take hundreds of thousands packets and days of capturing data can be accomplished today within 15 minutes with a mere 20k data frames. Simply put, cracking WEP is trivial.
We think she is taking a lot of pressure too.Can you pl guide us on what remedial actions we should take. She has Rahu dasa, budha anterdasa going on. She is very confused about what she wants to do after 12th. My daughter's details are as follows,DOB - Time of Birth: 11.48 amPlace of Birth: MumbaiPresently she is studying in 12th Science. Hindu astrology pdf download. Her Rahu, Venus and Budha are in 12th house with Rahu and Venus in ashlesha nakshatra and Budha in punarvasu.
WPA/WPA2-PSK encryption is holding its ground if using a strong, long key. However, weak passphrases are vulnerable to dictionary attacks. WPA/WPA2 may be on borrowed time as well, according to some recent news.
The WPS vulnerability renders even WPA/WPA2 secured wireless networks very vulnerable. An extensive list of vulnerable devices is available here: google docs spreadsheet. Note that some routers (including most popular Cisco/Linksys models) will NOT turn off WPS even if turned off via the radio button in their web admin interface. You may be able to turn it off using third-party firmware, such as DD-WRT (which does not support WPS).
Wifi Cracker Windows 8 Download
Related Links
aircrack-ng
reaver (WPS vulnerability)
WPA Wordlists - Torrent search
Openwall wordlist collection
Wordlists mirror
the A.R.G.O.N. - wordlists
Church of WiFi hash tables
The only potential problem under Windows is that fewer network adapters have compatible drivers that support monitor mode.

finnaly I got Back Track work (this allready took me a few time =) ) But now I typed in 'ifconfig' at the console but it doesn't show me a wirless interface. Do I need to install any drivers ? Or does it simply not work with my Laptop's Wirless Card. It's a Intel Wireless WiFi Link 5100. When I look at the compatibility list it should work I think :
Centrino a/g/n (5xxx) NO YES YES
Pls Help me.
Greetings Timothy
I have had no problem running aircrack with my Intel 4965agn wireless NIC as mentioned in the article.
Good luck
so im wondering. after this process, do i have to put my wireless card back in normal or 'managed' mode as i think its called? and if so how do i do so? thx a bunch in advance. i havent done this crack process yet cuz i want all the intangibles covered as much as i can but as soon as u reply, i will. cuz ur guide look legit and fool proof. thx again.
'ERROR: Neither the sysfs interface links nor the iw command is available'
when running airmon-ng start wlan0
it tells me to install iw but I found no easy way to install it.
Then again i'm running backtrack 3 from my usb dongle, I did not nor know how to install the image to the USB so I beleive the installation is readonly. Is it possible to install IW or how do I install backtrack to the USB dongle ?
Thanks for pointing me in the right direction
Alternatively, you can run Backtrack 3 from a live CD, or you can install some other version of Linux on a USB drive (or a second partition on your HDD).
Ultimately, it depends which OS supports the monitor/inject mode for your network card.
When I attempt to capture after entering the commands I get the following message:
'airodump-ng --help' for help
Nor is there a data file in my home folder, do you have any idea what I'm doing wrong?
Thanks.
airodump-ng --channel 6 --bssid 00:0F:CC:7D:5A:74 -w data mon0
This should work
Does it work with Mac OS X?
You can hide, and have hidden, behind the letter of the law.
Publishing this information is ethically criminal. Your disclaimer
clearly indicates you understand people will use this information
to do what ought not to be done. Namely hacking into networks
not their own. Shame on you speed guide !
WEP, for example, has very well known exploits, and anyone serious about securing their network should be aware of the extent of such flaws.
The article above merely informs readers how this is accomplished, therefore allowing them to make more educated choices when choosing encryption methods.
You have only to look at all the other posts here, in order to clearly understand what is happening. Others posting here are helping each other hack private networks (not protect themselves), whether you do or do not acknowledge this it doesn't change the truth of the matter. Period.
and that does jack what to my RADIUS setup?
I am extremely thankful to you for this informative, clean, pin pointed and easy to understand tutorial. It worked for me as piece of cake.
Before, I could reach at your article, I tried almost 50 Tutorials and 10 different Linux Distros. but my wireless RT2870 Chipset was not compatible for the said purpose.
Regards
Thank you again
Good work. Keep it up!
I have same intel 4965 agn with hp dv6985 se,Operating system Vista.I em using Vmware and running backtrack 3.I still cannot see my card.Please help me
Thanks